Matthew Garrett: Pluton is not (currently) a threat to software freedom
 At CES this week, Lenovo announced that their new Z-series laptops would ship with AMD processors that incorporate Microsoft's Pluton security chip. There's a fair degree of cynicism around whether Microsoft have the interests of the industry as a whole at heart or not, so unsurprisingly people have voiced concerns about Pluton allowing for platform lock-in and future devices no longer booting non-Windows operating systems. Based on what we currently know, I think those concerns are understandable but misplaced.
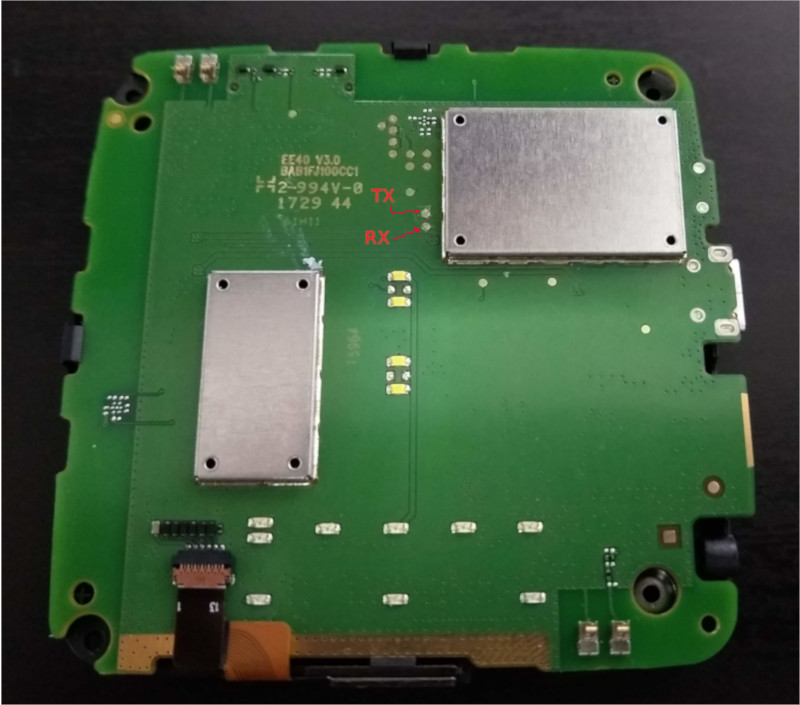
At CES this week, Lenovo announced that their new Z-series laptops would ship with AMD processors that incorporate Microsoft's Pluton security chip. There's a fair degree of cynicism around whether Microsoft have the interests of the industry as a whole at heart or not, so unsurprisingly people have voiced concerns about Pluton allowing for platform lock-in and future devices no longer booting non-Windows operating systems. Based on what we currently know, I think those concerns are understandable but misplaced.But first it's helpful to know what Pluton actually is, and that's hard because Microsoft haven't actually provided much in the way of technical detail. The best I've found is a discussion of Pluton in the context of Azure Sphere, Microsoft's IoT security platform. This, in association with the block diagrams on page 12 and 13 of this slidedeck, suggest that Pluton is a general purpose security processor in a similar vein to Google's Titan chip. It has a relatively low powered CPU core, an RNG, and various hardware cryptography engines - there's nothing terribly surprising here, and it's pretty much the same set of components that you'd find in a standard Trusted Platform Module of the sort shipped in pretty much every modern x86 PC. But unlike Titan, Pluton seems to have been designed with the explicit goal of being incorporated into other chips, rather than being a standalone component. In the Azure Sphere case, we see it directly incorporated into a Mediatek chip. In the Xbox Series devices, it's incorporated into the SoC. And now, we're seeing it arrive on general purpose AMD CPUs.
Microsoft's announcement says that Pluton can be shipped in three configurations:
as the Trusted Platform Module; as a security processor used for non-TPM scenarios like platform resiliency; or OEMs can choose to ship with Pluton turned off. What we're likely to see to begin with is the former - Pluton will run firmware that exposes a Trusted Computing Group compatible TPM interface. This is almost identical to the status quo. Microsoft have required that all Windows certified hardware ship with a TPM for years now, but for cost reasons this is often not in the form of a separate hardware component. Instead, both Intel and AMD provide support for running the TPM stack on a component separate from the main execution cores on the system - for Intel, this TPM code runs on the Management Engine integrated into the chipset, and for AMD on the Platform Security Processor that's integrated into the CPU package itself.
So in this respect, Pluton changes very little; the only difference is that the TPM code is running on hardware dedicated to that purpose, rather than alongside other code. Importantly, in this mode Pluton will not do anything unless the system firmware or OS ask it to. Pluton cannot independently block the execution of any other code - it knows nothing about the code the CPU is executing unless explicitly told about it. What the OS can certainly do is ask Pluton to verify a signature before executing code, but the OS could also just verify that signature itself. Windows can already be configured to reject software that doesn't have a valid signature. If Microsoft wanted to enforce that they could just change the default today, there's no need to wait until everyone has hardware with Pluton built-in.
The two things that seem to cause people concerns are remote attestation and the fact that Microsoft will be able to ship firmware updates to Pluton via Windows Update. I've written about remote attestation before, so won't go into too many details here, but the short summary is that it's a mechanism that allows your system to prove to a remote site that it booted a specific set of code. What's important to note here is that the TPM (Pluton, in the scenario we're talking about) can't do this on its own - remote attestation can only be triggered with the aid of the operating system. Microsoft's Device Health Attestation is an example of remote attestation in action, and the technology definitely allows remote sites to refuse to grant you access unless you booted a specific set of software. But there are two important things to note here: first, remote attestation cannot prevent you from booting whatever software you want, and second, as evidenced by Microsoft already having a remote attestation product, you don't need Pluton to do this! Remote attestation has been possible since TPMs started shipping over two decades ago.
The other concern is Microsoft having control over the firmware updates. The context here is that TPMs are not magically free of bugs, and sometimes these can have security consequences. One example is Infineon TPMs producing weak RSA keys, a vulnerability that could be rectified by a firmware update to the TPM. Unfortunately these updates had to be issued by the device manufacturer rather than Infineon being able to do so directly. This meant users had to wait for their vendor to get around to shipping an update, something that might not happen at all if the machine was sufficiently old. From a security perspective, being able to ship firmware updates for the TPM without them having to go through the device manufacturer is a huge win.
Microsoft's obviously in a position to ship a firmware update that modifies the TPM's behaviour - there would be no technical barrier to them shipping code that resulted in the TPM just handing out your disk encryption secret on demand. But Microsoft already control the operating system, so they already have your disk encryption secret. There's no need for them to backdoor the TPM to give them something that the TPM's happy to give them anyway. If you don't trust Microsoft then you probably shouldn't be running Windows, and if you're not running Windows Microsoft can't update the firmware on your TPM.
So, as of now, Pluton running firmware that makes it look like a TPM just isn't a terribly interesting change to where we are already. It can't block you running software (either apps or operating systems). It doesn't enable any new privacy concerns. There's no mechanism for Microsoft to forcibly push updates to it if you're not running Windows.
Could this change in future? Potentially. Microsoft mention another use-case for Pluton "as a security processor used for non-TPM scenarios like platform resiliency", but don't go into any more detail. At this point, we don't know the full set of capabilities that Pluton has. Can it DMA? Could it play a role in firmware authentication? There are scenarios where, in theory, a component such as Pluton could be used in ways that would make it more difficult to run arbitrary code. It would be reassuring to hear more about what the non-TPM scenarios are expected to look like and what capabilities Pluton actually has.
But let's not lose sight of something more fundamental here. If Microsoft wanted to block free operating systems from new hardware, they could simply mandate that vendors remove the ability to disable secure boot or modify the key databases. If Microsoft wanted to prevent users from being able to run arbitrary applications, they could just ship an update to Windows that enforced signing requirements. If they want to be hostile to free software, they don't need Pluton to do it.
(Edit: it's been pointed out that I kind of gloss over the fact that remote attestation is a potential threat to free software, as it theoretically allows sites to block access based on which OS you're running. There's various reasons I don't think this is realistic - one is that there's just way too much variability in measurements for it to be practical to write a policy that's strict enough to offer useful guarantees without also blocking a number of legitimate users, and the other is that you can just pass the request through to a machine that is running the appropriate software and have it attest for you. The fact that nobody has actually bothered to use remote attestation for this purpose even though most consumer systems already ship with TPMs suggests that people generally agree with me on that)

 Active noise cancellation (ANC) has been all the rage lately in the headphones
and in-ear monitors market. It seems after Apple got heavily praised for their
AirPods Pro, every somewhat serious electronics manufacturer released their
own design incorporating this technology.
The first headphones with ANC I remember trying on (in the early 2010s) were
the Bose QuietComfort 15. Although the concept did work (they indeed cancelled
some sounds), they weren't amazing and did a great job of convincing me ANC
was some weird fad for people who flew often.
Active noise cancellation (ANC) has been all the rage lately in the headphones
and in-ear monitors market. It seems after Apple got heavily praised for their
AirPods Pro, every somewhat serious electronics manufacturer released their
own design incorporating this technology.
The first headphones with ANC I remember trying on (in the early 2010s) were
the Bose QuietComfort 15. Although the concept did work (they indeed cancelled
some sounds), they weren't amazing and did a great job of convincing me ANC
was some weird fad for people who flew often.
 As the years passed, chip size decreased, battery capacity improved and machine
learning blossomed truly a perfect storm for the wireless ANC headphones
market. I had mostly stayed a sceptic of this tech until recently a kind friend
offered to let me try a pair of Sony WH-1000X M3.
Having tested them thoroughly, I have to say I'm really tempted to buy them
from him, as they truly are fantastic headphones
As the years passed, chip size decreased, battery capacity improved and machine
learning blossomed truly a perfect storm for the wireless ANC headphones
market. I had mostly stayed a sceptic of this tech until recently a kind friend
offered to let me try a pair of Sony WH-1000X M3.
Having tested them thoroughly, I have to say I'm really tempted to buy them
from him, as they truly are fantastic headphones I won't be keeping them though.
Whilst I really like what Sony has achieved here, I've grown to understand ANC
simply isn't for me. Some of the drawbacks of ANC somewhat bother me: the ear
pressure it creates is tolerable, but is an additional energy drain over long
periods of time and eventually gives me headaches. I've also found ANC
accentuates the motion sickness I suffer from, probably because it messes up
with some part of the inner ear balance system.
Most of all, I found that it didn't provide noticeable improvements over good
passive noise cancellation solutions, at least in terms of how high I have to
turn the volume up to hear music or podcasts clearly. The human brain works in
mysterious ways and it seems ANC cancelling a class of noises (low hums,
constant noises, etc.) makes other noises so much more noticeable. People
talking or bursty high pitched noises bothered me much more with ANC on than
without.
So for now, I'll keep using my trusty Senheiser HD 280 Pro
I won't be keeping them though.
Whilst I really like what Sony has achieved here, I've grown to understand ANC
simply isn't for me. Some of the drawbacks of ANC somewhat bother me: the ear
pressure it creates is tolerable, but is an additional energy drain over long
periods of time and eventually gives me headaches. I've also found ANC
accentuates the motion sickness I suffer from, probably because it messes up
with some part of the inner ear balance system.
Most of all, I found that it didn't provide noticeable improvements over good
passive noise cancellation solutions, at least in terms of how high I have to
turn the volume up to hear music or podcasts clearly. The human brain works in
mysterious ways and it seems ANC cancelling a class of noises (low hums,
constant noises, etc.) makes other noises so much more noticeable. People
talking or bursty high pitched noises bothered me much more with ANC on than
without.
So for now, I'll keep using my trusty Senheiser HD 280 Pro My
My 









 DebConf21 is taking place online, from 24 August to 28 August 2021.
It is the 22nd Debian conference, and organizers and participants are working hard
together at creating interesting and fruitful events.
We would like to warmly welcome the 19 sponsors of DebConf21, and introduce them to you.
We have five Platinum sponsors.
Our first Platinum sponsor is
DebConf21 is taking place online, from 24 August to 28 August 2021.
It is the 22nd Debian conference, and organizers and participants are working hard
together at creating interesting and fruitful events.
We would like to warmly welcome the 19 sponsors of DebConf21, and introduce them to you.
We have five Platinum sponsors.
Our first Platinum sponsor is 

 Added memory to ACER Chromebox CXI3 (fizz/sion).
Got 2 16GB SO-DIMMs and installed them. I could not find correct information on how to open this box on the internet. They seem to be explaining similar boxes from HP or ASUS which seem to have simpler procedure to opening.
I had to ply out out the 4 rubber pieces at the bottom, and then open the 4 screws.
Then I could ply open the front and back panel by applying force where the screws were.
In the front panel there's two more shorter screws that needs to be opened; after taking out the two screws (that's 4+2),
I could open the box into two pieces. Be careful they are connected, I think there's audio cable.
After opening you can access the memory chips. Pull the metal piece open on left and right hand side of the memory chip so that it raises. Make sure the metal pieces latch closed when you insert the new memory, that should signify memory is in place. I didn't do that at the beginning and the machine didn't boot.
So far so good. No longer using zram.
Added memory to ACER Chromebox CXI3 (fizz/sion).
Got 2 16GB SO-DIMMs and installed them. I could not find correct information on how to open this box on the internet. They seem to be explaining similar boxes from HP or ASUS which seem to have simpler procedure to opening.
I had to ply out out the 4 rubber pieces at the bottom, and then open the 4 screws.
Then I could ply open the front and back panel by applying force where the screws were.
In the front panel there's two more shorter screws that needs to be opened; after taking out the two screws (that's 4+2),
I could open the box into two pieces. Be careful they are connected, I think there's audio cable.
After opening you can access the memory chips. Pull the metal piece open on left and right hand side of the memory chip so that it raises. Make sure the metal pieces latch closed when you insert the new memory, that should signify memory is in place. I didn't do that at the beginning and the machine didn't boot.
So far so good. No longer using zram.



 They also provided a set of feet allowing for vertical mounting of the device, which was a nice touch.
The USB/SATA bridge chip in use has changed; the original was:
They also provided a set of feet allowing for vertical mounting of the device, which was a nice touch.
The USB/SATA bridge chip in use has changed; the original was:
 My mistake was going poking around trying to figure out where the updates are downloaded from - I know I m running a slightly older release than what s current, and the device can do an automatic download + update. Top tip; don t run
My mistake was going poking around trying to figure out where the updates are downloaded from - I know I m running a slightly older release than what s current, and the device can do an automatic download + update. Top tip; don t run  Over the course of the last year and a half, I ve been doing some self-directed
learning on how radios work. I ve gone from a very basic understanding of
wireless communications (there s usually some sort of antenna, I guess?) all
the way through the process of learning about and implementing a set of
libraries to modulate and demodulate data using my now formidable stash of SDRs.
I ve been implementing all of the RF processing code from first principals and
purely based on other primitives I ve written myself to prove to myself that I
understand each concept before moving on.
I figured that there was a fun capstone to be done here - the blind reverse
engineering and implementation of the protocol my cheep Amazon power switch
uses to turn on and off my Christmas Tree. All the work described in this post
was done over the course of a few hours thanks to help during the demodulation
from
Over the course of the last year and a half, I ve been doing some self-directed
learning on how radios work. I ve gone from a very basic understanding of
wireless communications (there s usually some sort of antenna, I guess?) all
the way through the process of learning about and implementing a set of
libraries to modulate and demodulate data using my now formidable stash of SDRs.
I ve been implementing all of the RF processing code from first principals and
purely based on other primitives I ve written myself to prove to myself that I
understand each concept before moving on.
I figured that there was a fun capstone to be done here - the blind reverse
engineering and implementation of the protocol my cheep Amazon power switch
uses to turn on and off my Christmas Tree. All the work described in this post
was done over the course of a few hours thanks to help during the demodulation
from  After taking a capture, I started to look at understanding what the modulation
type of the signal was, and how I may go about demodulating it.
Using
After taking a capture, I started to look at understanding what the modulation
type of the signal was, and how I may go about demodulating it.
Using 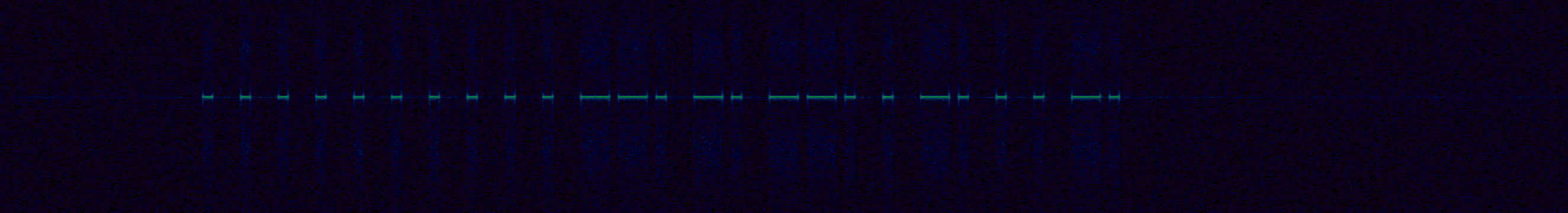 Next, I started to measure the smallest pulse, and see if I could infer the
symbols per second, and try to decode it by hand. These types of signals are
generally pretty easy to decode by eye.
Next, I started to measure the smallest pulse, and see if I could infer the
symbols per second, and try to decode it by hand. These types of signals are
generally pretty easy to decode by eye.


 After some googling, I found a single lone
After some googling, I found a single lone
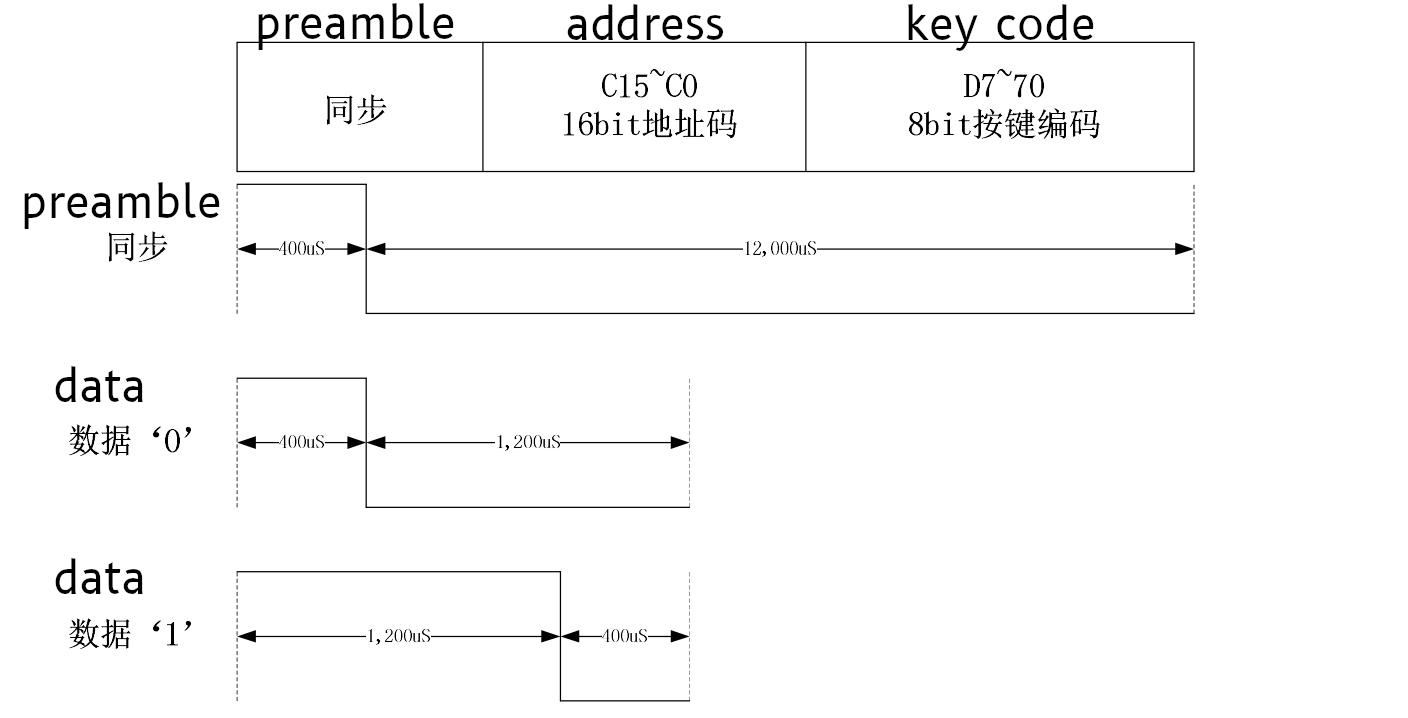 It s a bummer that we missed the clock sync / preamble pulse before the data
message, but that s OK somehow. It also turns out that 8 or 10 bit series of of
0"s wasn t clock sync at all - it was part of the address! Since it also turns
out that all devices made by this manufacturer have the hardcoded address of
It s a bummer that we missed the clock sync / preamble pulse before the data
message, but that s OK somehow. It also turns out that 8 or 10 bit series of of
0"s wasn t clock sync at all - it was part of the address! Since it also turns
out that all devices made by this manufacturer have the hardcoded address of
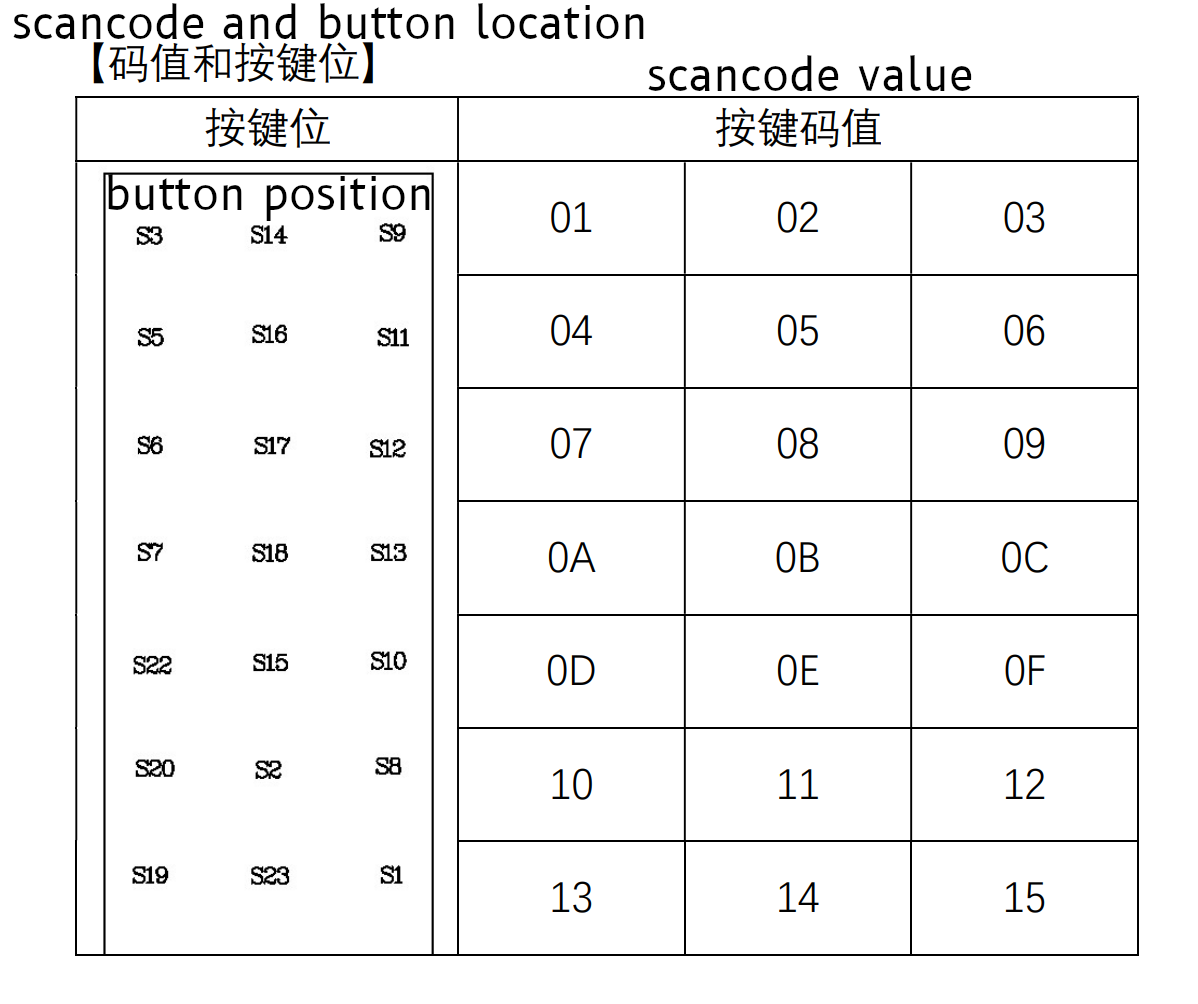 And even more interestingly, one of our scancodes ( Off , which is 0x94) shows up just
below this table, in the examples.
And even more interestingly, one of our scancodes ( Off , which is 0x94) shows up just
below this table, in the examples.
 Over all, I think this tells us we have the right bits to look at for
determining the scan code! Great news there!
Over all, I think this tells us we have the right bits to look at for
determining the scan code! Great news there!
 I have an original
I have an original 




